DHCP Server¶
The IPv4 DHCP server assigns IPv4 addresses and related configuration options to client PCs on a network. It is enabled by default on the LAN interface with a default range of 192.168.56.100 through 192.168.56.199. In this default configuration, the firewall assigns its LAN IP address (192.168.56.1) as the gateway and DNS server if either the DNS Resolver or DNS Forwarder is enabled. There are numerous options available in the web interface, which are covered in the next section.
Configuration
To alter the behavior of the IPv4 DHCP server, navigate to Services > DHCP Server in the web interface. The behavior of the IPv4 DHCP server is controlled there, along with static IP address mappings and related options such as static ARP.
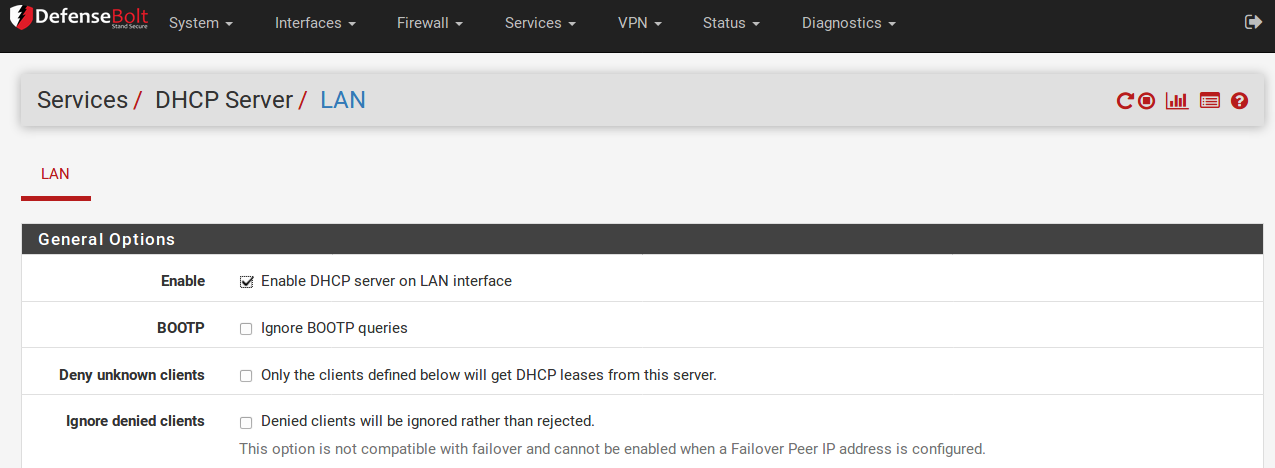
Choosing an Interface
The DHCP configuration page contains a tab for each interface with a static IP address. Each interface has its own separate DHCP server configuration, and they may be enabled or disabled independently of one another. Before making any changes, visit the tab for the correct interface.
General Options¶
Enable The first setting on the tab enables or disables DHCP service for the interface. To turn on DHCP for the interface, check Enable DHCP server on [name] interface. To disable the service, uncheck the box instead.
Deny unknown clients Under normal circumstances,the DHCP server will answer requests from any client requesting a lease. In most environments this is normal and acceptable behavior, but in restricted or secure environments this behavior is undesirable. With this option set, only clients with static mappings defined will receive leases. This is a more secure practice but is much less convenient. This option is per-pool, meaning that if unknown clients are denied in the default range, another pool of IP addresses may be defined that does not have the setting checked. The DHCP server will assign clients IP addresses out of that alternate pool instead.
Note
This will protect against low-knowledge users and people who casually plug in devices. Be aware, however, that a user with knowledge of the network could hardcode an IP address, subnet mask, gateway, and DNS which will still give them access. They could also alter/spoof their MAC address to match a valid client and still obtain a lease. Where possible, couple this setting with static ARP entries, access control in a switch that will limit MAC addresses to certain switch ports for increased security, and turn off or disable unused switch ports.
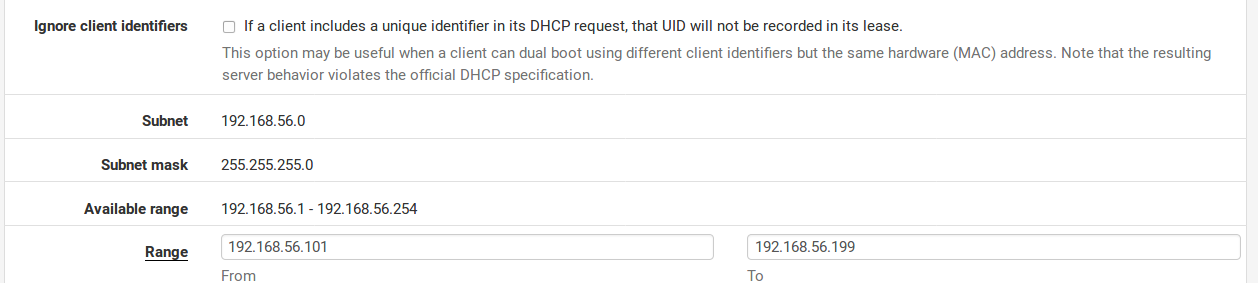
Subnet The network address of the interface subnet, for reference purposes.
Subnet Mask The subnet mask for the interface subnet, for reference purposes.
Available Range The range of available addresses inside the interface subnet, for referenceand to help etermine the desired range for DHCP clients. The network address and broadcast address are excluded, but interface addresses and Virtual IP addresses are not excluded.
Range This defines the DHCP address range, also referred to as the Scope or Pool. The two boxes for Range tell the firewall the first and last address for use as a DHCP pool. Addresses between the entered values, inclusive, will be used for clients which request addresses via DHCP. The range must be entered with the lower number first, followed by the higher number. For example, the default LAN DHCP range is based off of the subnet for the default LAN IP address. It is 192.168.56.100 to 192.168.56.199. This range can be as large or as small as the network needs, but it must be wholly contained within the subnet for the interface being configured.
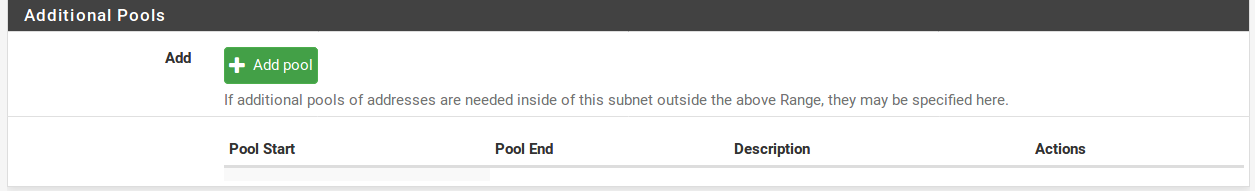
Additional Pools¶
The Additional Pools section defines extra pools of addresses inside of the same subnet. These pools can be used to craft sets of IP addresses specifically for certain clients, or for overflow from a smaller original pool, or to split up the main pool into smaller chunks with a GAP of non-DHCP IP addresses in the middle of what used to be the pool. A combination of the MAC Address Control options may be used to guide clients from the same manufacturer into a specific pool, such as VoIP phones.
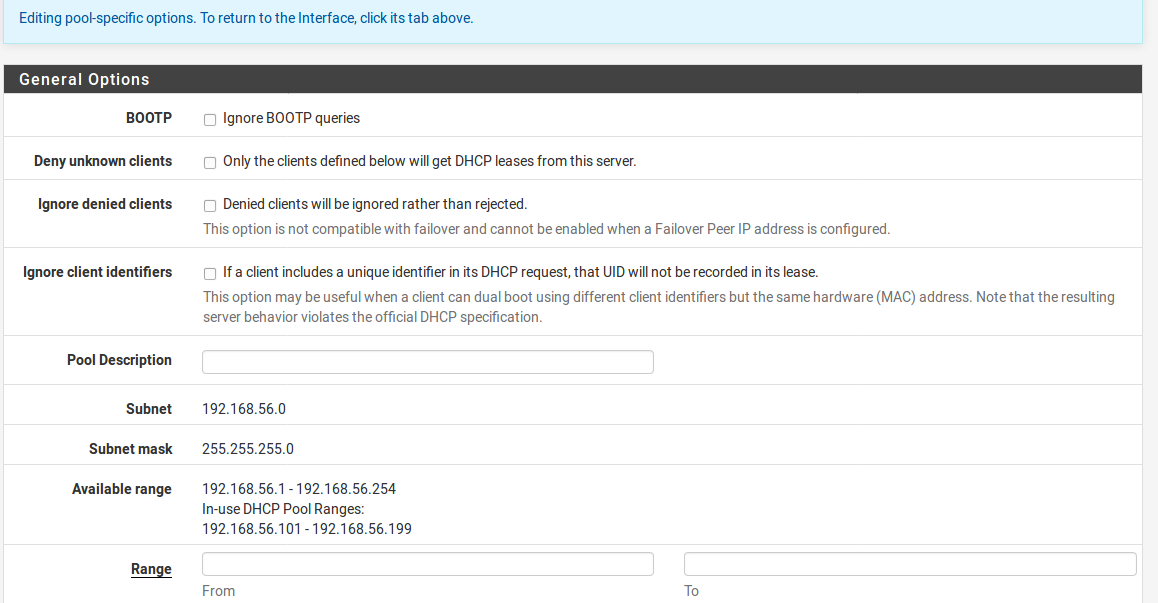
To add a new pool, click pluse butten Add Pool and the screen will switch to the pool editing view, which is nearly the same as the normal DHCP options, except a few options that are not currently possible in pools are omitted. The options behave the same as the others discussed in this section. Items left blank will, by default, fall through and use the options from the main DHCP range.
Note
See the MAC Address Control section below for specifics on directing clients into or away from pools.
Servers¶
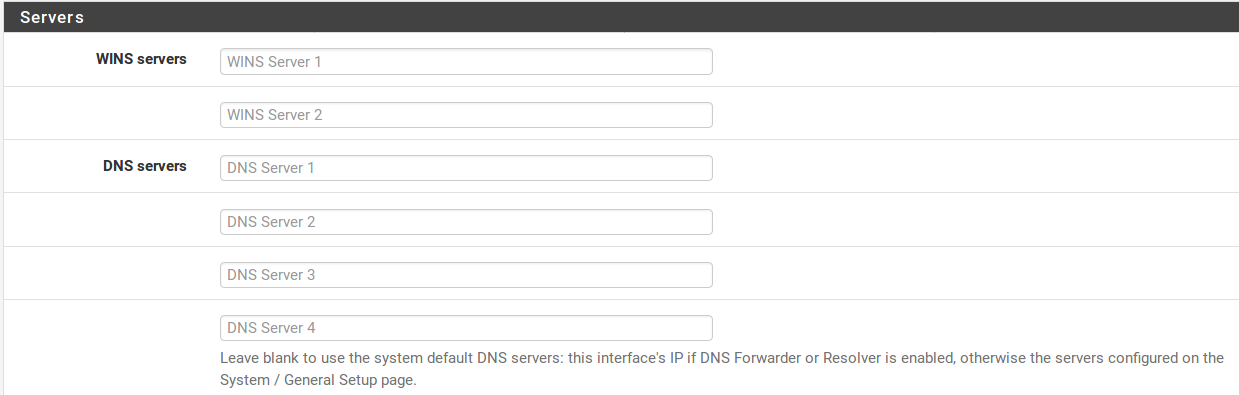
WINS Servers Two WINS Servers (Windows Internet Name Service) may be defined that will be passed on to clients. If one or more WINS serversis required, enter their IP addresses here. The actual servers do not have to be on this subnet, but be sure that the proper routing and firewall rules are in place to let them be reached by client PCs. If this is left blank, no WINS servers will be sent to the client.
DNS Servers The DNS Servers may or may not need filled in, depending on the firewall configuration. If the built-in DNS Resolver or DNS Forwarder is used to handle DNS, leave these fields blank and DefenseBolt will automatically assign itself as the DNS server for client PCs. If the DNS forwarder is disabled and these fields are left blank, DefenseBolt will pass on whichever DNS servers are defined under System > General Setup. To use custom DNS Servers instead of the automatic choices, fill in the IP addresses for up to four DNS servers here. In networks with Windows servers, especially those employing Active Directory, it is recommended to use those servers for client DNS. When using the DNS Resolveror DNS forwarder in combination with CARP, specify the CARP Virtual IP address on this interfacehere.
Other Options¶
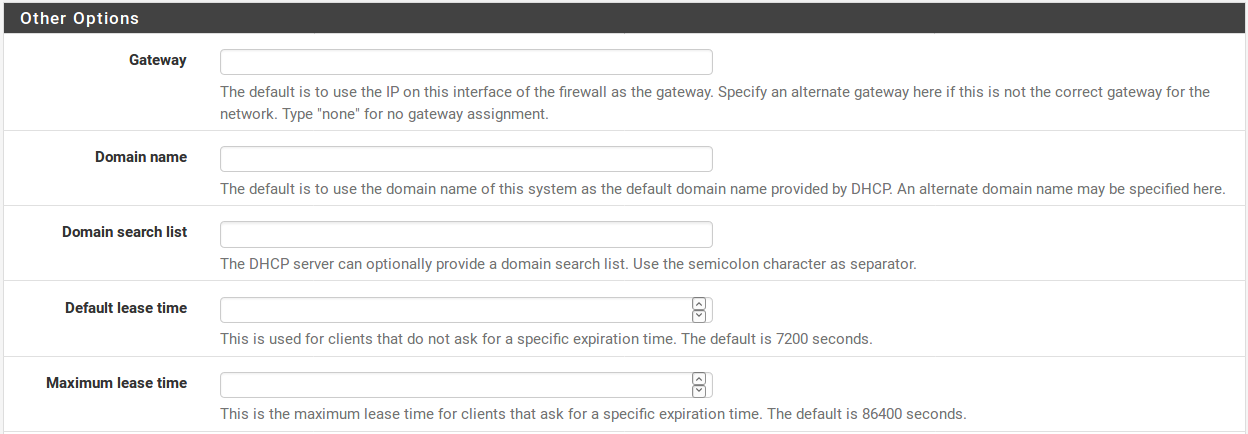
Gateway This may also be left blank if this firewall is acting as the gateway for the network on this interface. If that is not the case, fill in the IP address for the gateway to be used by clients on this interface. When using CARP, fill in the CARP Virtual IP address on this interface here.
Domain Name Specifies the domain name passed to the client to form its fully qualified hostname. If the Domain Name is left blank, then the domain name of the firewall it sent to the client. Otherwise, the client is sent this value.
Domain Search List Controls the DNS search domains that are provided to the client via DHCP. If multiple domains are present and short hostnames are desired, provide a list of domain names here, separated by a semicolon. Clients will attempt to resolve hostnames by adding the domains, in turn, from this list before trying to find them externally. If left blank, the Domain Name option is used.
Note
The Domain Search List is provided viaDHCP option 119. As of this writing, no Windows DHCP client of any version supports DHCP option 119. Other operating systems such as BSD, Linux, and OS X do support obtaining the Domain Search List via DHCP option 119.
Default lease time Controls how long a lease will last when a client does not request a specific lease length. Specified in seconds, default value is 7200 seconds (2 hours)
Maximum lease time Limits a requested leaselength to a stated maximum amount of time. Specified in seconds, default value is 86400 seconds (1 day).
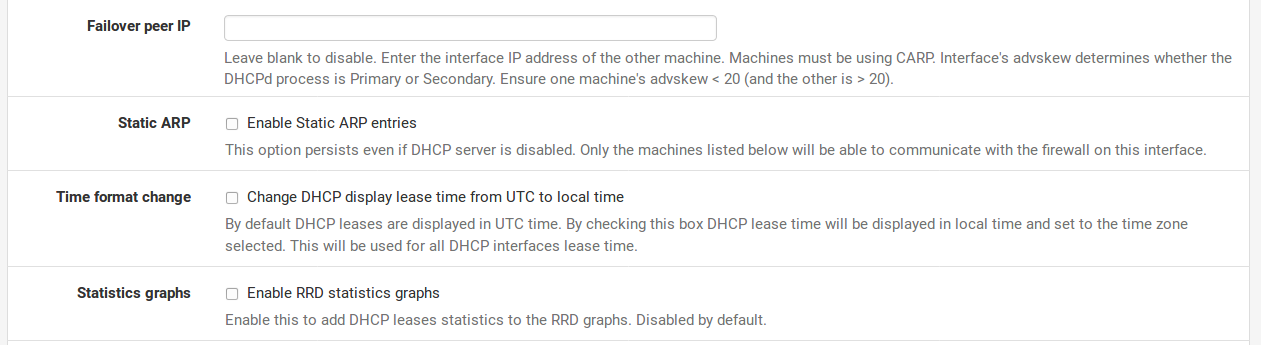
Failover Peer IP If this system is part of a High Availability failover cluster, enter the real IP address of the other system in this subnet here. Do not enter a CARP Virtual IP address.
Static ARP This checkbox works similar to denying unknown MAC addresses from obtaining leases, but takes it a step further in that it also restricts any unknown MAC address from communicating with this firewall. This stops would- be abusersfrom hardcoding an unused address on this subnet, circumventing DHCP restrictions.
Note
When using static ARP, all systems that need to communicate with the firewall must be listed in static mappings before activating this option, especially the system being used to connect to the DefenseBolt GUI. Also be aware that this option may prevent people from hardcoding an IP address and talking to the firewall, but it does not preventthem from reaching each other on the local network segment.
Time Format Change By default, the ISC DHCP daemon maintains lease times in UTC. When this option is checked, the times on the DHCP Leases status page are converted to the local time zone defined on the firewall.
Statistics Graphs This option, disabled by default, activates RRD graphing for monitoring the DHCP pool utilization.

Dynamic DNS
For Dynamic DNS settings, click Display Advanced to the right of that field, which displays the following options:
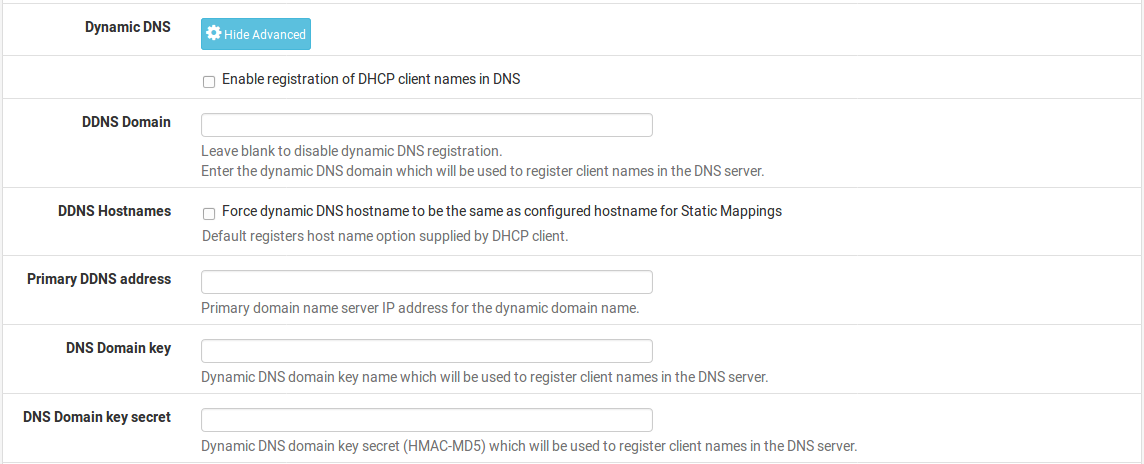
Enable Check the box to enable registration of DHCP client names in DNS using an external (non-DefenseBolt) DNS server.
DDNS Domain The domain name used for registering clients in DNS
Primary DDNS Address The DNS server used for registering clients in DNS DNS Domain Key The encryption key used for DNS registration
DNS Domain Key Secret The secret for the key used for DNS registration

MAC Address Control
For MAC Address Control, click Display Advanced to show the lists of allowed and denied client MAC addresses. Each list is comma-separated and contains portions of MAC addresses. For example, a group of VoIP phones from the same manufacturer may all start with the MAC address aa:bb:cc. This can be leveraged to give groups of devices or users separate DHCP options.
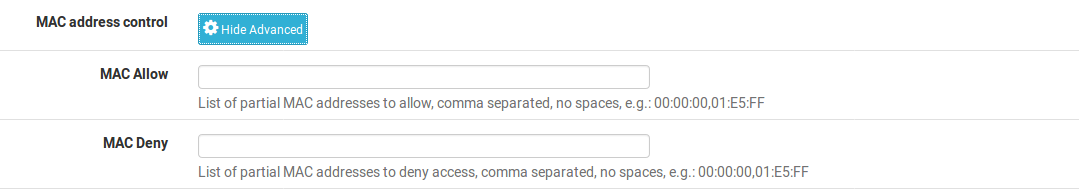
Allow A list of MAC Addresses to allow in this pool. If a MAC address is in the allow box, then all others will be denied except the MAC address specified in the allow box. Deny A list of MAC Addresses to deny from this pool. If a MAC address is in the deny list, then all others are allowed.
It is best to use a combination of allow and deny to get the desired result, such as: In the main pool, leave allow blank and deny aa:bb:cc. Then in the VoIP pool, allow aa:bb:cc. If that extra step is not taken to allow the MAC prefix in the additional pool, then other non-VoIP phone clients could receive IP addresses from that pool, which may lead to undesired behavior.
This behavior may also be used to blacklist certain devices from receiving a DHCP response. For example to prevent Example brand printers from receiving a DHCP address, if MAC addresses all start with ee:ee:ee, then place that in the deny list of each pool.

NTP Servers
To specify NTP Servers (Network Time Protocol Servers), click the Display Advanced button to the right of that field, and enter IP addresses for up to two NTP servers.
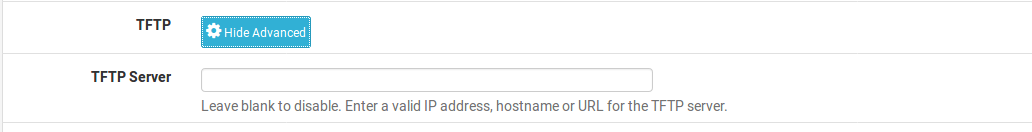
TFTP Server
click the Display Advanced button next to TFTP to display the TFTP server option. The value in the TFTP Server box, if desired, must be an IP address or hostname of a TFTP server. This is most often used for VoIP phones, and may also be referred to as “option 66” in other documentation for VoIP and DHCP.
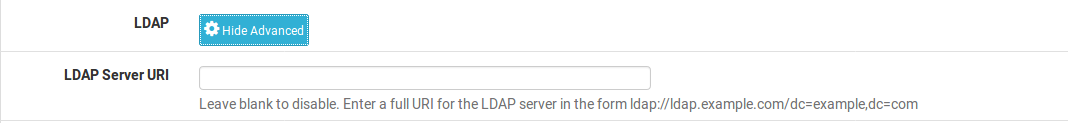
LDAP URI
click the Display Advanced button next to LDAP to display the LDAP Server URI option. LDAP Server URI will send an LDAP server URI to the client if requested. This may also be referred to as DHCP option 95. It takes the form of a fully qualified LDAP URI, such as ldap://ldap.example.com/dc=example,dc=com. This option can help clients using certain kinds of systems, such as OpenDirectory, to find their server.

Additional BOOTP/DHCP Options
Other numeric DHCP options can be sent to clients using the Additional BOOTP/DHCP Options controls. To view these options, click Display Advanced in this section. To add a new option, click pluse Add.
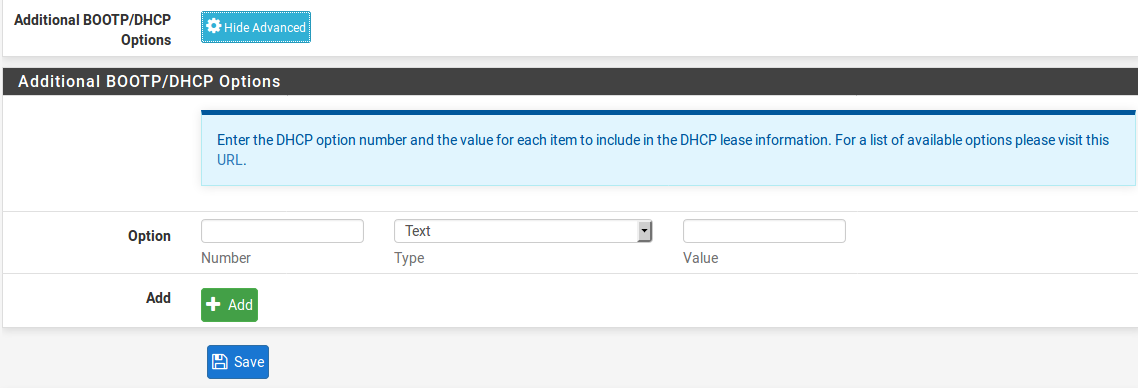
Number The DHCP option code number. IANA maintains a list of all valid DHCP options.
Type The choices and formats for each type may be a little counter-intuitive, but the labels are used directly from the DHCP daemon. The proper uses and formats are
Text Free-form text to be sent in reply, such http://www.example.com/wpad/wpad.dat or Example Company. as
String A string of hexadecimal digits separated by a colon, such as c0:a8:05:0c.
Boolean Either true or false.
Unsigned 8, 16, or 32-bit Integer A positive Integer that will fit within the given data size, such as 86400.
Signed 8, 16, or 32-bit Integer A positive or negative Integer that will fit within the given data size, such as -512. IP address or host An IP address such as 192.168.56.1 or a hostname such as www.example.com.
Value The value associated with this numeric option and type.
For more information on which options take a specific type or format, see the linked list above from the IANA.
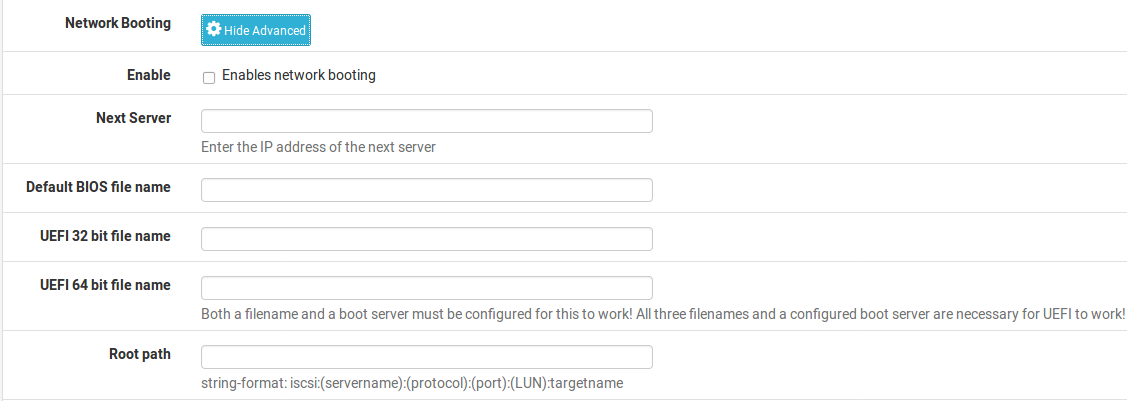
Network Booting
To view the Network boot settings, click pluse button in the Network Booting section header bar. Enable Check to enable network booting options in DHCP
Next Server The IP address from which boot images are available.
Default BIOS file name File name for the boot image (Non-UEFI)
UEFI 32 bit file name File for 32-bit UEFI booting
UEFI 64 bit file name File for 64-bit UEFI booting
Root Path String to target a specific device as the client’s root filesystem device, such as
iscsi:(servername):(protocol):(port):(LUN):targetname.
Save Settings
After making changes, click Save before attempting to create static mappings. Changes to settings willbe lost if the browser leaves this page without saving.
DHCP Static Mappings¶
Static DHCP mappings express a preference for which IP address will be assigned to a given client based on its MAC address. In a network where unknown clients are denied, this also serves as a list of “known” clients which are allowed to receive leases or have static ARP entries. Static mappings can be added in one of two ways:
- From this screen, click pluse butten Add.
- Add them from the DHCP leases view, which is covered later in this chapter.
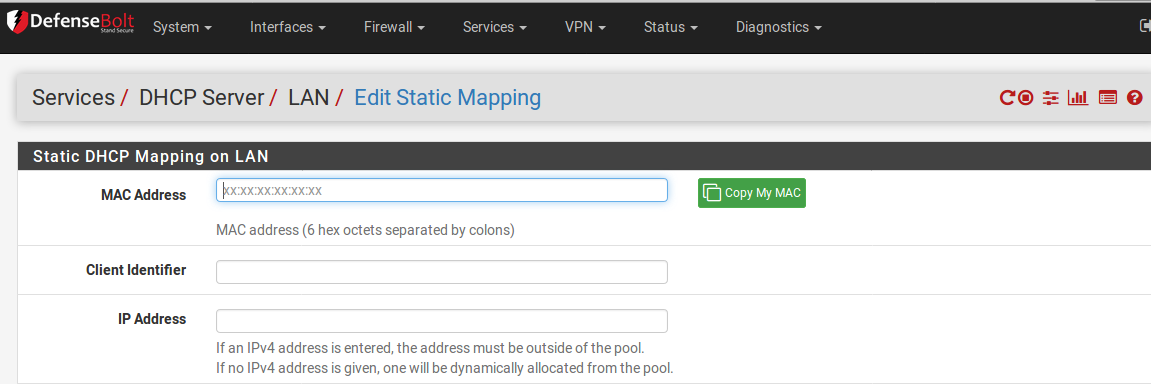
On this screen, only the MAC address is necessary.
MAC Address The client MAC address which identifies the host to deliver options on this page, or by entering only the MAC address, it will be added to the list of known clients for use when the Deny unknown clients option is set.
Note
Client MAC address can be obtained from a command prompt on most platforms. On UNIX-based or UNIX-work-alike operating systems including Mac OS X, typing ifconfig -a will show the MAC address for each interface. On Windows-based platforms, ipconfig /all will show the MAC address. The MAC address may also sometimes be found upon a sticker on the network card, or near the network jack for integrated adapters. For hosts on the same subnet, the MAC can be determined by pinging the IP address of the host and then running arp - a.
Client Identifier An ID sent by the client to identify itself.
IP Address The IP address field is needed if this will be a static IP address mapping instead of only informing the DHCP server that the client is valid. This IP address is a preference, not a reservation. Assigning an IP address here will not prevent someone else from using the same IP address. If this IP address is in use when this client requests a lease, it will instead receive an address from the general pool. For this reason, the DefenseBolt WebGUI does not allow assigning static IP mappings inside of the DHCP pool.
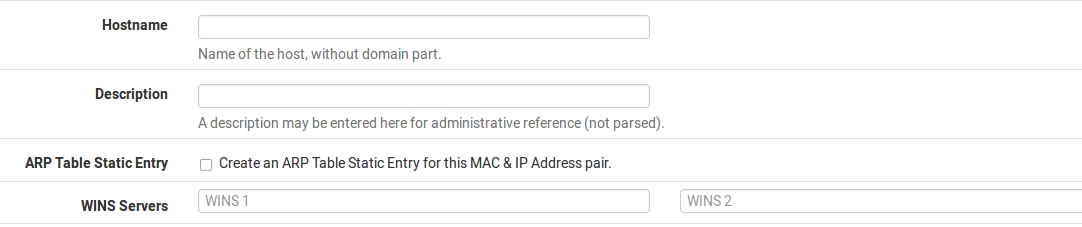
Hostname The hostname of the client. This does not have to match the actual hostname set on the client. The hostname set here will be used when registering DHCP addresses in the DNS forwarder.
Description Cosmetic only, and available for use to help track any additional information about this entry. It could be the name of the person who uses the PC, its function, the reason it needed a static address, or the administrator who added the entry. It may also be left blank.
ARP Table Static Entry If checked, this entry will receive a static ARP entry in the OS tying this IP address to this MAC address.
Note
If this option is used rather than using the global static ARP option, it does not prevent that MAC address from using other IP addresses, it only prevents other MAC addresses from using this IP address. In other words, it prevents another machine from using that IP to reach the firewall, but it doesn’t stop the user from changing their own IP address to something different.
Note
The remaining options available to set for this client are the same in behavior to the ones found earlier in this section for the main DHCP settings.
Click Save to finish editing the static mapping andreturn to the DHCP Server configuration page.
Status¶
The status of the DHCP server service itself is at Status > Services. If the DHCP server is enabled, its status will be shown as Running, as in Figure DHCP Daemon Service Status. The buttons on the right side allow restarting or stopping the DHCP server daemon. Restarting is not normally necessary as DefenseBolt will automatically restart the service when configuration changes are made that require a restart. Stopping the service is also likely not necessary, as the service will stop when all instances of the DHCP server are disabled.
Leases¶
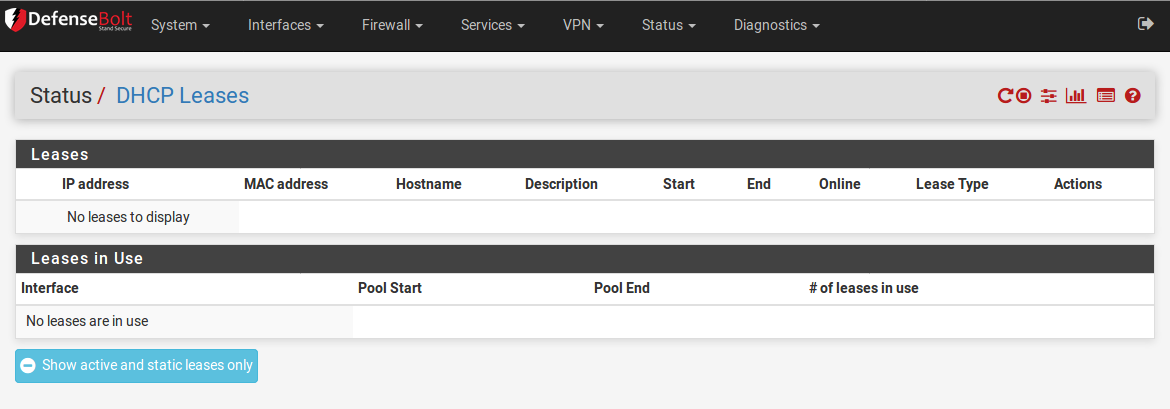
The currently assigned DHCP leases are viewable at Status > DHCP leases. This page shows various aspects of the client leases. These include:
- The assigned IP address
- The client MAC address
- The hostname (if any) that the client sent as part of the DHCP request
- The description for a host with a DHCP static mapping
- The beginning and end times of the lease
- Whether or not the machine is currently online (in the firewall’s ARP table)
- Whether or not the lease is active, expired, or a static registration
View inactive leases
By default, only active and static leases are shown, but everything, including the expired leases, may be displayed by clicking Show all configured leases. To reduce the view back to normal, click Show active and static leases only.
View inactive leases
By default, only active and static leases are shown, but everything, including the expired leases, may be displayed by clicking Show all configured leases. To reduce the view back to normal, click Show active and static leases only.
Wake on LAN Integration
Clicking the Power butten icon to the right of the lease sends a Wake on LAN (WOL) packet to that host. Click Pulse butten to create a WOL entry for the MAC address instead. For more details about Wake on LAN, see Wake on LAN.
Add static mapping
To create a static mapping from a dynamic lease, click the to the right of the lease. This will pre-fill the MAC address of that host into the Edit static mapping screen. Add the desired IP address, hostname and description and click Save.
Delete a lease
While viewing the leases, an inactive or expired lease may be manually deleted by clicking This option is not available for active or static leases, only for offline or expired leases. at the end of its line.
DHCP Service Logs The DHCP daemon will log its activity to Status > System Logs, on the DHCP tab. Each DHCP request and response will be displayed, along with other status and error messages.