Dynamic DNS¶
The Dynamic DNS client built into DefenseBolt registers the IP address of a WAN interface with a variety of dynamic DNS service providers. This is used to remotely access services on hosts that have WANs with dynamic IP addresses, most commonly VPNs, web servers, and so on. Any number of Dynamic DNS clients may be configured using any of over 20 different Dynamic DNS providers, or even custom Dynamic DNS providers. Dynamic DNS clients can use any WAN, and can even register the real public IP address in environments where the firewall receives a private IP address for its WAN and is NATed upstream.
In addition to the typical HTTP/HTTPS-based Dynamic DNS providers, DefenseBolt also supports RFC 2136 style Dy-namic DNS updates directly to DNS servers.
Dynamic DNS and IPv6
As of this writing, there are very few Dynamic DNS providers that offer IPv6 support. The available choices are limited to HE.net when they host DNS for a domain, custom types, and RFC 2136 servers.
Configuring a Dynamic DNS Client
DefenseBolt allows registration with many different dynamic DNS providers. The available providers may be viewed by clicking the Service Type selector. More information about the providers may be found by searching for their name to find their web site. Several offer a basic level service at no cost, and some offer additional premium services at a cost. There is also a Custom option that allows for a custom URL to accommodate an unsupported provider.
Select a provider, visit their website, register for an account, and setup a hostname. The procedures for this vary with each provider, but they all have instructions on their websites. After configuring a hostname with a provider, configure DefenseBolt with matching settings. Most providers have the same, or similar options. There are a few types with custom options that will be covered later in this section.
To configure a Dynamic DNS client:
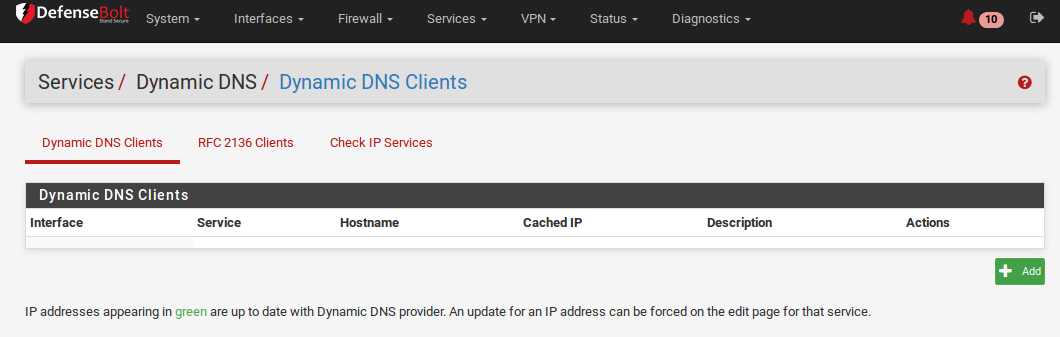
- Navigate to Services > Dynamic DNS
- Click pluse Add to add a new entry
- Configure the options as follows:
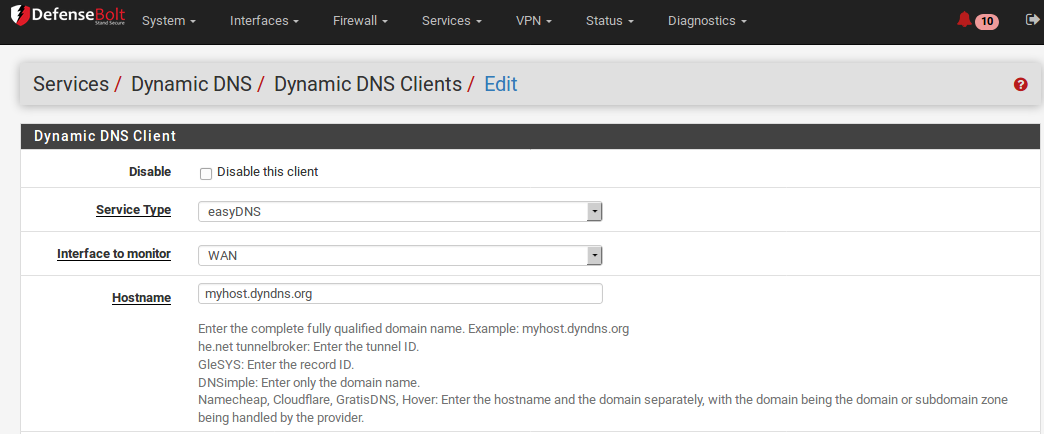
Disable Check to disable the entry, or leave unchecked so it will be active.
Service Type Select the dynamic DNS provider here.
Interface to Monitor Select the interface that has the IP address to keep updated, such as WAN, or an OPTx interface. Selecting a gateway group for the interface allows the Dynamic DNS entry to switch between WANs so it can allow inbound Multi-WAN failover of services on this hostname.
Hostname Enter the hostname created at the dynamic DNS provider. This is typically the complete fully qualified domain name, such as myhost.example.com, except for Namecheap where this is only the host portion of the address.
Domain Name For Namecheap hosts, this box must be set to the domain part of the full hostname.
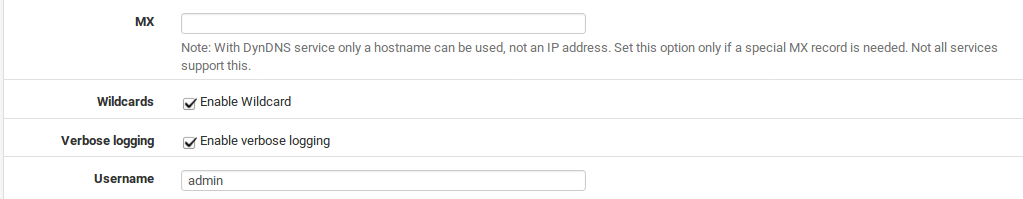
MX An MX (Mail Exchanger) record is how Internet mail servers know where to deliver mail for a domain. Some dynamic DNS providers will let MX records be configured via the dynamic DNS client. If the chosen proider allows this, enter the host name of the mail server that will receive Internet mail for the dynamic DNS domain.
Wildcards When wildcard DNS is enabled on a dynamic DNS name, all host name queries under the given domain will resolve to the IP address of the dynamic DNS host name. For example, if the host name is example.dyndns.org, enabling wildcard will make*.example.dyndns.org (a.example.dyndns.org, b.example.dyndns.org, etc.) resolve the same as example.dyndns.org.
Verbose Logging Check this option to increase the logging for the Dynamic DNS update process, which is useful for troubleshooting update problems.
Verify SSL Peer When checked, the SSL certificate of the DynDNS provider server will be validated. Some servers with self-signed certificates, or those using a less common CA, may require this to be set.
Username Enter the username for the dynamic DNS provider. Provider-specific requirements:
Namecheap, FreeDNS Leave blank
Route 53 Enter the Access Key ID
GleSYS Enter the API user
Custom The username is used with basic HTTP authentication and may be left blank.
Password Enter the password for the dynamic DNS provider. Provider-specific requirements:
Namecheap, FreeDNS This is the Authentication Token
Route 53 Enter the Secret Access Key
GleSYS Enter the API Key
DNSimple Enter the API Token
Description A text field for reference.
- Click Save
Providers with Extra or Different Settings
Some providers have special settings or certain fields that need to be set in a specific way that may not be obvious. The differences are outlined in this section.
Namecheap As mentioned earlier in the settings above, Namecheap requires that the fully qualified domain name be split into the hostname part and domain name part in separate fields.
When setting up Dynamic DNS for a Namecheap domain, an authentication token is given by Namecheap. This goes in the Password field, and the Username field is left blank.
HE.net Tunnelbroker The HE.net Tunnelbroker choice updates an IPv6 tunnel endpoint IP address when the WANIP changes. The Hostname in this case is the Tunnel ID from HE.net.
Route 53 When using an Amazon Route 53 type, the Username is the Access Key ID provided by Amazon.
The following additional options are available when using Route 53:
Verify SSL Peer Enable to verify the server certificate when using HTTPS
Zone ID Received when creating the domain in Route 53. Must be filled in.
TTL Time to Live for the the DNS record.
Custom The Custom Dynamic DNS type configures options that allow for updating otherwise unsupported services. When using the custom Dynamic DNS type, the Username and Password fields are sent using HTTP basic authentication.
The following additional options are available when using Custom:
Interface to send update from Almost always the same as the Interface, but can be changed as needed.
Force IPv4 Resolving When checked, the update host will only be resolved using IPv4
Verify SSL Peer Enable to verify the server certificate when using HTTPS
Update URL The URL given by the Dynamic DNS provider for updates. If the IP address must appear in the URL, enter it as %IP% and the real value will be substituted as needed.
Result Match Defines expected output from the Dynamic DNS query. If it succeeds and matches the output given, then DefenseBolt will know that the update was successful. If it does not match exactly, then it is assumed that the update failed. Leave empty to disable result checking.
DNSSimple
Verify SSL Peer Enable to verify the server certificate when using HTTPS
Zone ID Received when creating the domain.
TTL Time to Live for the the DNS record.
Configuring RFC 2136 Dynamic DNS updates
RFC 2136 Dynamic DNS registers a hostname on any DNS server supporting RFC 2136 style updates. This can be used to update DNS records on BIND and Windows Server DNS servers, amongst others.
RFC 2136 Dynamic DNS entries may be used at the same time as regular style Dynamic DNS service providers, and like those, any number of entries can be created. RFC 2136 will update the A record, and the AAAA record if IPv6 is configured on the monitored interface.
Configuring the server infrastructure for RFC 2136 Dynamic DNS hosting is beyond the scope of this book, but there is a basic how-to on the pfSense documentation wiki that covers setting up BIND to handle RFC 2136 updates.
To configure an RFC 2136 Dynamic DNS client:
- Navigate to Services > Dynamic DNS
- Click the RFC 2136 tab
- Click pluse Add to add a new entry
- Configure the options as follows:
Enable Controls whether or not the entry is active. If it is unchecked, updates will not be performed for this entry.
Interface The IP address on the chosen interface will be sent when performing the DNS update.
Hostname The fully qualified domain name (FQDN) of the dynamic DNS entry to update. For example, myhost.example.com.
TTL The Time To Live for the DNS entry, in seconds. Higher values will be cached longer by other name servers, so lower values are better to be sure that DNS updates are picked up in a timely manner by other servers. Usually a value between 30 and 180 seconds is reasonable, depending on how often the IP address changes.
Key Name The name of the key as specified in the DNS server configuration. For Host keys, this is typically the FQDN, so it would be identical to the value in the Hostname field. For Zone keys this would be the name of the DNS zone.
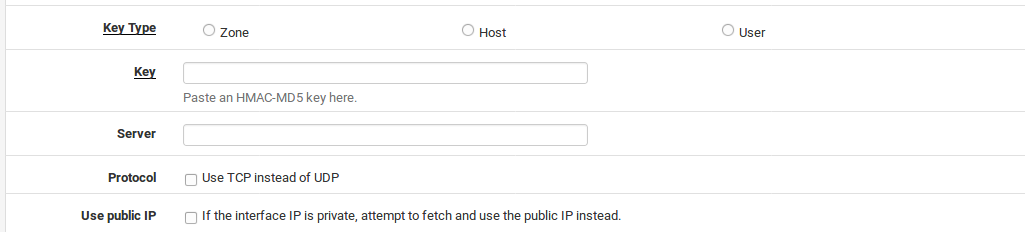
Key Type Can be one of Zone, Host or User. The type of key is determined by the server, so consult the server configuration or the DNS server administrator to determine the Key Type. Typically this is set to Host.
Key Contains the actual text of the key, e.g. /0/4bxF9A08n/zke/vANyQ==. This value is generated by the DNS server or administrator.
Server The IP address or hostname of the DNS server to which updates are sent.
Protocol When unchecked, the DNS update is sent over UDP, when checked it uses TCP instead.
Use Public IP By default, the interface IP address is always sent to the name server for the DNS update. If this box is checked, when a private IP address is detected on the selected Interface, a check is done to determine what the actual public IP address is, and then that IP address is used for the DNS update.
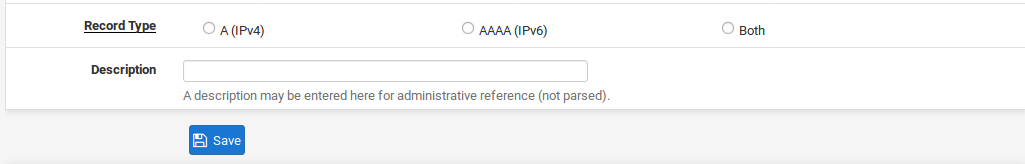
Record Type Determines which record(s) will be updated for this entry. For the IPv4 address, use A, for IPv6, use AAAA, or choose Both.
Description A free-text description of the entry for reference.
As with the other Dynamic DNS types, RFC 2136 updatesare performed only when an IP address change is detected, or once every 25 days.