PPPoE Server¶
DefenseBolt can act as a PPPoE server, accepting and authenticating connections from PPPoE clients on a local interface, in the role of an access concentrator (LAC). This feature can be used to force users to authenticate before gaining network access, or otherwise control their login behavior.
The PPPoE Server is located at Services > PPPoE Server. The configuration is very similar to the L2TP VPN server (L2TP VPN).
Multiple PPPoE servers may be configured on separate interfaces. To begin setting up a PPPoE server:
- Navigate to Services > PPPoE Server
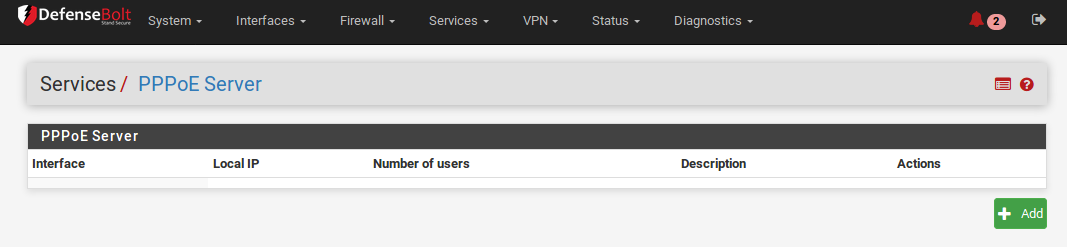
- Click pluse Add to add a new server entry
- Configure the PPPoE Server as follows:
Enable When checked, this PPPoE Server instance will be active.
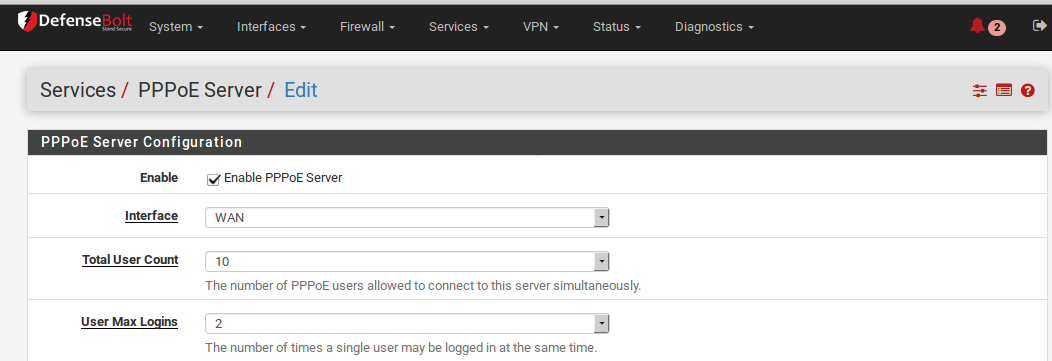
Interface The single interface upon which PPPoE service will be available.
Total User Count Determines how many clients in total are allowed to connect to this instance.
User Max Logins Determines how many times a single client may login concurrently.
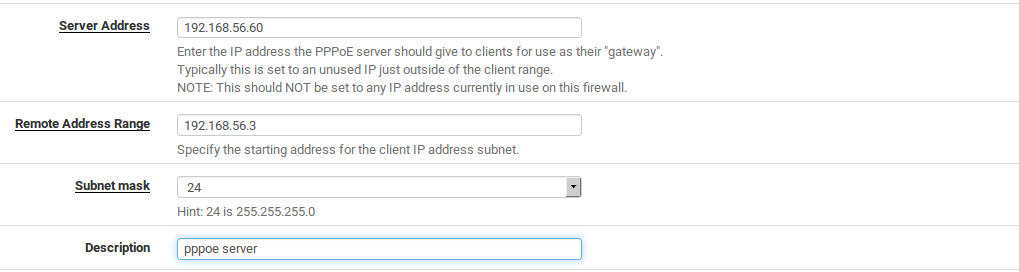
Server Address The IP address which the pfSense system will send to the PPPoE clients to use as their gateway.
Warning
This IP address must not be an IP address currently in use on the firewall.
Remote Address Range The IP address for the start of the PPPoE client subnet. Together with the
Subnet Mask it defines the network used by the PPPoE clients. Subnet Mask Defines the CIDR mask assigned to PPPoE clients.
Description Optional explanatory text for this server instance.
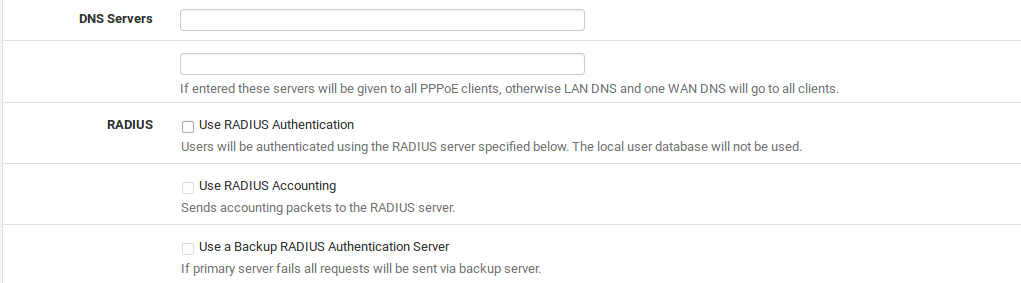
DNS Servers Optional fields used to send specific DNS servers to the PPPoE clients, otherwise the firewall IP address will be sent to the client for DNS if the DNS Forwarder or DNS Resolver are enabled. If the DNS Forwarder and DNS Resolver areboth disabled, then the DNS servers configured on the firewall will be sent instead
- Configure RADIUS if that will be utilized for user authentication. Any RADIUSserver may be used.
See also:
See RADIUS Authentication with Windows Server for information on setting up RADIUS on a Windows server.
Use RADIUS Authentication Check to configure the PPPoE server to use at least one RADIUS server for Authentication instead of local users.
Use RADIUS Accounting Optional, sends RADIUS accounting data to the RADIUS server to note items such as login and logout times, and bandwidth used.
Use a Backup RADIUS Authentication Server A second RADIUS server to use if the primary RADIUS server fails.
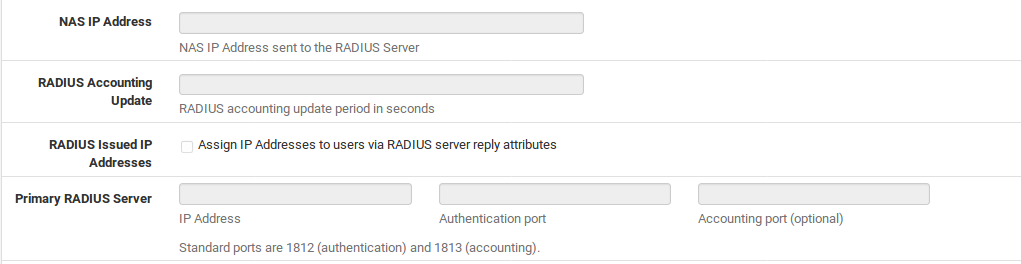
NAS IP Address Optional, sends a specific IP address to the RADIUS server for the NAS-IP Address attribute.
RADIUS Accounting Update The interval at which accounting data is sent to the RADIUS server, in seconds.
RADIUS Issued IP Addresses When checked, IP addresses can be assigned to users via RADIUS reply attributes.
Primary RADIUS Server The preferred RADIUS server to use for Authentication.
IP Address The IP address of the RADIUS server
Authentication Port The port used for authentication (typically 1812)
Accounting Port The port used for accounting data (typically 1813)
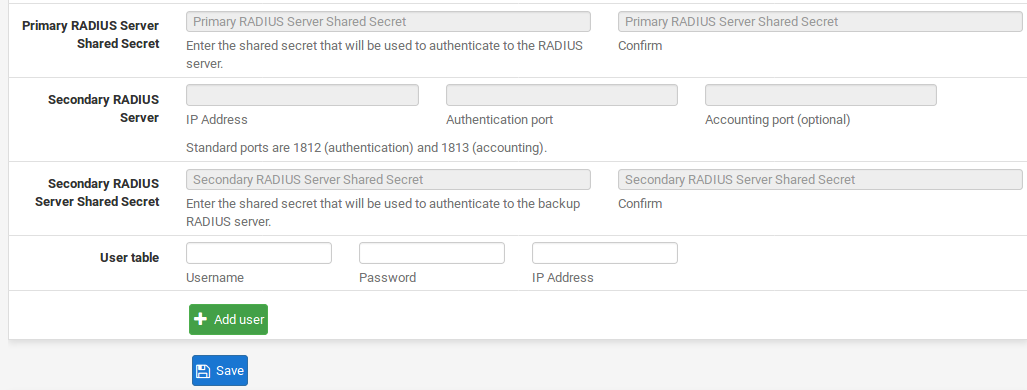
Primary RADIUS Server Shared Secret The shared secret configured for this firewall on the RADIUS server. The same value must be entered in the Confirm box.
Secondary RADIUS Server Same type of settings as the primary, but defines the secondary RADIUS server. - Add users to the server to utilize local authentication: - Click pluse Add User
Username The username for the user account
Password The password for the user account
IP Address An optional static IP address to assign the user at login
- Repeat as needed
- Click Save
rule¶
Now, all that remains to be done is to add a firewall rule to allow traffic to permit traffic from PPPoE clients. Navigate to Firewall -> Rules and click on the PPPoE Server tab. Once there, click on the plus button to add a new rule.
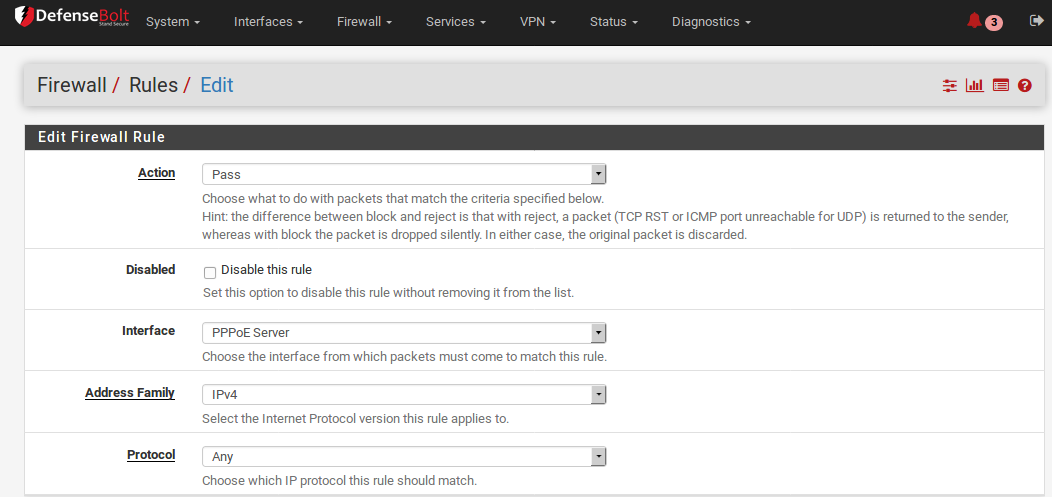
- At Action,
- choose Pass,
- at Interface, choose PPPoEVPN.
- For Protocol, select any.
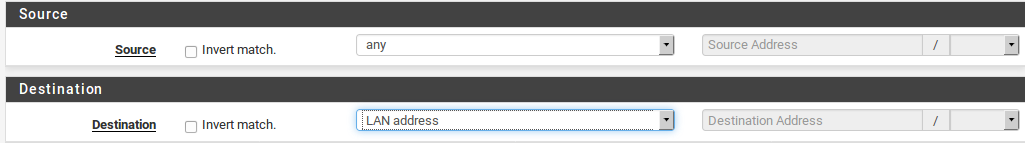
- for Destination, select the target destination for PPPoE clients (e.g. LAN subnet).
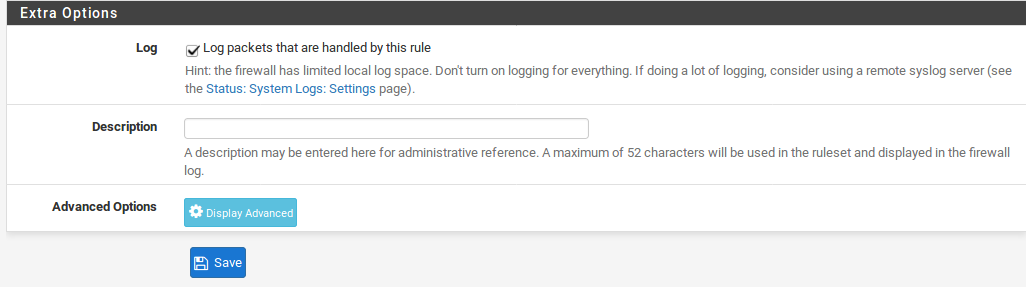
You can probably keep Log packets that are handled by this rule” unchecked, and at Description, enter an appropriate description. Finally, press the Save button to save changes, and Apply changes to apply the changes. Once the rule has been created, our DefenseBolt PPPoE server will be ready for tobe accesse.